If you are reading this post, you may possibly be interested in the stack overflow vulnerability on the Netgear WG6024, published here.
The vulnerability can be triggered by logging into the device and changing his admin password to something a bit longer than 128 characters.
This can be done by sending a proper POST request to the web server: either via some purposely written code or bypassing client side checks on the dedicated web page on the management interface
In both ways an overly long password will be saved in flash memory and will be used during authentication, overflowing a buffer on the stack and allowing for remote code execution.
In any case password will be “permanently” changed, web server will crash at each authentication attempt and reverting to a sane situation may require resetting the whole device, losing the whole configuration.
Reset can be performed by pressing the little button on the rear side of the device for more than 20 seconds, but, another solution is possible by using the serial interface present on the access point’s board, shown in the picture below along with its pinout.
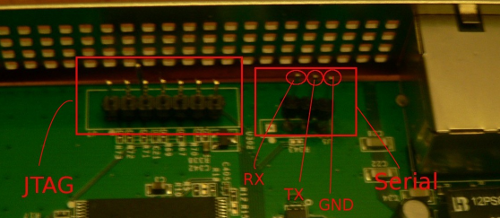
That is a 3.3V TTL serial interface that can be used by means of proper a TTL-USB converter.
Please note that the connector is originally unpopulated in the stock AP, so I needed to solder some pins on the board, in order to connect to the serial interface with my TTL-USB converter and start a normal session over the serial interface.
Once connected, password can be restored by using the nvram command and restarting the AP in the following way:
nvram set http_passwd=password && nvram commit && /sbin/reboot |
nvram set http_passwd=password && nvram commit && /sbin/reboot
The password will be changed to “password” and will not overflow the buffer anymore; the web server will not crash during authentication and the web management interface can then be accessed in the usual way.
The whole AP configuration will remain untouched and will not force the victim (you? ;)) to go through the annoying re-configuration process.
